With over 40% of all websites around the world being powered by WordPress security, its global adoption makes it an attractive target among cybercriminals. This is why a proactive security
With over 40% of all websites around the world being powered by WordPress security, its global adoption makes it an attractive target among cybercriminals. This is why a proactive security strategy is essential among developers, administrators, and security professionals managing WordPress environments. In this guide, we have explained the common vulnerabilities that arise in WordPress and the preventive measures that can be implemented to strengthen the security against threats.
Understanding WordPress Cyberattacks
Administrative Account Exploitation
Creation of an unsolicited administrator-level account is the primary indicator for a breach in a WordPress site. To evade detection, these accounts are often registered using deceptive email addresses that resemble official accounts (for example, admin@wordpress.org). These fake accounts provide uninterrupted access to your website, even after the password is changed.
Factors Enabling the Attacks
Some of the common factors that make WordPress a target for cybercrimes are:
- Weak Credentials – Weak usernames and passwords that are easy to guess fall prey to brute force.
- Unpatched Security Elements – Outdated core, theme, or plugins can make the environment vulnerable.
- Malicious Plugins – Intentional backdoors or hostile coding are often disguised as functional plugins.
- SQL Injection – Harmful input fields that enable the manipulation of database queries.
- Cross-site Scripting – Exploitative coding scripts that are injected into the site through comment fields, forms, or third-party extensions.
Essential Strategies for WordPress Security
Following are the fundamental security measures that you can adopt to protect your site against hacking:
1. Secure User Management
Maintaining a clean and monitored database is pertinent for WordPress security. Review and address unauthorized access effectively using:
SQL Cleanup Commands:
-- Remove suspicious users
DELETE FROM wp_users WHERE user_login = 'unauthorized_user@example.com';
-- Clean up related usermeta entries
DELETE FROM wp_usermeta WHERE user_id NOT IN (SELECT ID FROM wp_users);Automated User Filtering via Email Domain:
To enforce domain-level access control, deploy the following function in functions.php:
php
function remove_unwanted_users_by_domain() {
global $wpdb;
$allowed_domain = '@outrightcrm.com';
$users_to_delete = $wpdb->get_results("
SELECT ID FROM {$wpdb->users}
WHERE user_email NOT LIKE '%{$allowed_domain}'
");
foreach ($users_to_delete as $user) {
wp_delete_user($user->ID);
}
}
add_action('init', 'remove_unwanted_users_by_domain');
2. Limitations on User Registrations
To effectively manage user access and reduce the area of exposure for cyberattacks, you can implement the following measures:
- Single Administrator Regime – Maintain a single administrative profile, if feasible.
- Regulated Registration – User registrations should be need-specific with permission requirements.
- Data Export – Data pertaining to registered users should be exported to an external system (such as Brevo, SendGrid, or CRM platforms) before cleansing from WordPress.
This minimises the threat factors for database attacks, while lead data can be preserved externally.
3. Region-Specific Restrictions for Login Access
For websites with users from different countries around the world, region-specific restrictions can be imposed to reduce unauthorized login attempts.
function restrict_login_by_country() {
// Allowed Country Code (Change this to your country)
$allowed_country = 'IN'; // Example: 'IN' for India, 'US' for USA
if (strpos($_SERVER['REQUEST_URI'], 'wp-login.php') !== false) {
$user_ip = $_SERVER['REMOTE_ADDR'];
$geo_data = json_decode(file_get_contents("http://ipinfo.io/{$user_ip}/json"));
if (isset($geo_data->country) && $geo_data->country !== $allowed_country) {
wp_die("Access restricted! You are not allowed to log in from your location.");
}
}
}
add_action('init', 'restrict_login_by_country');Note: The above implementation harnesses a third-party service (ipinfo.io) which may have rate limits. For production setups, a geolocation API or security plugin would be more ideal.
4. Configuration Management for Security
Sensitive credentials should not be incorporated within configuration files (wp-config.php). To avoid exposure, use environment variables or adopt a .env file approach such as:
In wp-config.php:
define('DB_NAME', getenv('DB_NAME'));
define('DB_USER', getenv('DB_USER'));
define('DB_PASSWORD', getenv('DB_PASSWORD'));
define('DB_HOST', getenv('DB_HOST')); For local development with .env file:
if (file_exists(dirname(__FILE__) . '/.env')) {
$env = parse_ini_file('.env');
foreach ($env as $key => $value) {
putenv("$key=$value");
}
} Advanced Strategies for WordPress Security
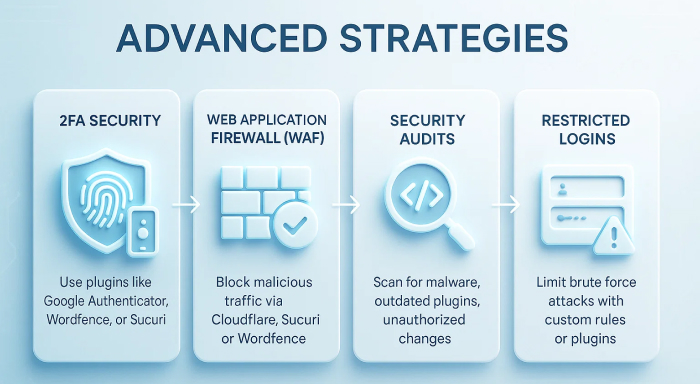
To further enhance your website’s security against malicious attacks, the following advanced practices can be implemented:
1. Two-Factor Authentication (2FA)
2FA provides an added layer of security, as it requires a secondary factor to verify the users’ credentials. Recommended WordPress plugins that facilitate 2FA are:
- Google Authenticator
- Wordfence
- Sucuri Security
2. Web Application Firewall (WAF)
A WAF detects and filters malicious or blacklisted HTTP traffic (both incoming and outgoing) to protect your site against exploitative attack. Some reliable WAF service providers include:
- Cloudflare
- Sucuri
- Wordfence
3. Routine Security Audits
Schedule routine evaluations of your WordPress ecosystem to:
- Perform malware scanning for suspicious codes
- Review user accounts and access control
- Detect and update outdated plugins, themes, or core
- Monitor unauthorised file changes using plugins
4. Restricted Login Attempts
To protect your website against brute force attacks, limit the login attempts with plugins or custom code such as:
function limit_login_attempts() {
if (strpos($_SERVER['REQUEST_URI'], 'wp-login.php') !== false && $_SERVER['REQUEST_METHOD'] === 'POST') {
$ip = $_SERVER['REMOTE_ADDR'];
$transient_name = 'login_attempts_' . md5($ip);
$attempts = get_transient($transient_name) ?: 0;
if ($attempts >= 5) {
wp_die('Too many failed login attempts. Please try again later.');
}
// Increment attempts only on failed login
add_action('wp_login_failed', function() use ($ip, $transient_name, $attempts) {
set_transient($transient_name, $attempts + 1, HOUR_IN_SECONDS);
});
}
}
add_action('init', 'limit_login_attempts');
Note: The above function restricts login after 5 attempts per IP address.
Monitoring and Recovery
Despite the implementation of preventive security measures, cybercriminals might still manage to breach your site. That is why it is crucial to plan an incident management and recovery strategy that incorporates:
1. Regular Off-Site Automated Backups
Schedule automated backups for routine intervals to store your data in remote locations. Some tools offering backup services are:
- UpdraftPlus
- BackupBuddy
- Reliable hosting providers
2. Event Logging and Tracking
Maintain a record of all logins and security-related events on your WordPress site using:
function log_security_events($user_login, $user) {
$log_file = ABSPATH . 'security-log.txt';
$time = current_time('mysql');
$ip = $_SERVER['REMOTE_ADDR'];
$log_message = "{$time} | User: {$user_login} | IP: {$ip} | Login successful\n";
file_put_contents($log_file, $log_message, FILE_APPEND);
}
add_action('wp_login', 'log_security_events', 10, 2); This will enable you to monitor and track anomalies. You can also integrate it with centralised systems such as CRMs for real-time alerts.
3. Response Protocol
Devise a clear and concise incident response protocol that involves:
- Detection and containment of the breach.
- Isolation and cleaning of the infected files.
- Resetting all password credentials.
- Restoration of data from a clean backup source.
- Identification of the root cause to enhance security measures.
Conclusion
WordPress security is not a one-time task; it is a dynamic process with recurring workflow due to ever evolving cyberattacks. The proactive implementation of the strategies mentioned above can secure your WordPress site to significantly reduce risks and downtime.
Key Takeaways:
- Manage user accounts and remove unauthorised registrations.
- Review and update WordPress core, themes, and plugins at regular intervals.
- Apply region-specific restriction if needed.
- Implement credential monitoring and management (2FA).
- Automate regular backups.
Respond to this article with emojis