Penetration testers repeatedly emphasize that identity breaks everything. Firewalls stand tall, EDR blinks confidently, and then one overprivileged account walks straight through the front door. This cycle recurs across banks,
Penetration testers repeatedly emphasize that identity breaks everything. Firewalls stand tall, EDR blinks confidently, and then one overprivileged account walks straight through the front door. This cycle recurs across banks, startups, governments, and even the entire circus industry. The attack paths don’t start with exotic zero‑days; they start with bad decisions in identity stores. So, the modern pentest findings reads less like “hackers bypassed controls” and more like “the organization handed them a master key.” That pattern isn’t a fluke. It’s a design failure, industrialized and exported everywhere, proudly and consistently.
The Myth Of The Single Breach Point
Security leaders still love the movie script: one dramatic exploit, one heroic fix. Pen testers keep handing them something uglier. The first villain typically appears as a forgotten service account with outdated permissions. The modern pentest findings highlight identity sprawl, not advanced payloads. And here’s the twist: automated pentest reporting now exposes recurring identity flaws at scale, so no one can claim ignorance. The access graph looks like a plate of spaghetti. Attackers don’t break one door. They just climb the entire, rotting staircase of inherited rights and lazy exceptions.
Overprivileged Access As Default Setting
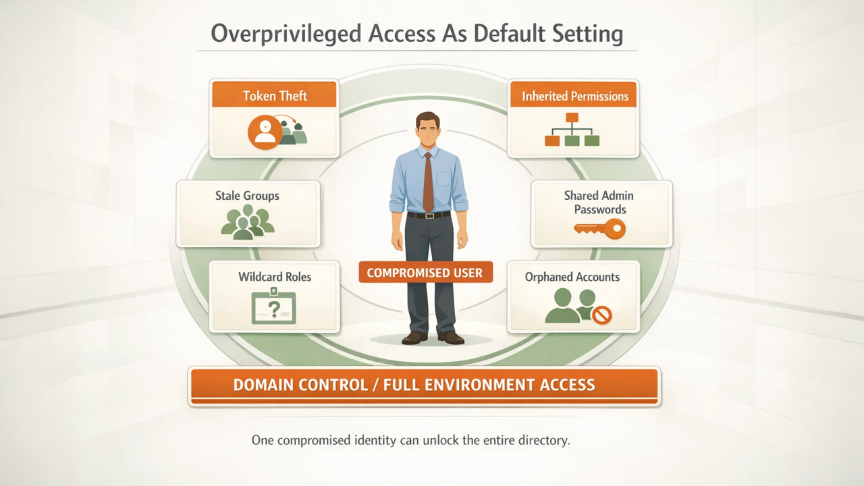
Most organizations treat “least privilege” as a talking point rather than a rule. So, accounts gain permissions like barnacles on a ship. And once a tester compromises any user, the blast radius turns absurd. The directory contains shared admin passwords, wildcard roles, and stale groups from projects that ended five years ago. That junk never dies. The directory becomes a graveyard of old exceptions and emergency workarounds. And every grave opens at the attackers' discretion. Nobody needs zero‑day exploits when a basic user can pivot to domain control in three clicks, one token theft, and a misconfigured role.
SSO, MFA, and the Illusion Of Safety
SSO arrives, everyone applauds, and the board thinks the access risk has vanished. It didn’t. It consolidated. Now, a single identity broker controls everything, which means a single compromise controls the entire system. Pentest findings reveal that session theft, consent phishing, and weak conditional access policies effectively bypass attractive login screens. MFA provides assistance, but only until misconfigured exclusions and legacy protocols allow attackers to gain access. So, the security stack glows green while refresh tokens drift across unmanaged devices. The company emphasizes convenience, whereas attackers emphasize centralization and its generous single point of failure.
Cloud Entitlements: The Hidden Attack Highway
Cloud turned permission models into chaos engines. Penetration tests conducted on cloud environments often reveal alarming permission-related issues. A single role within a single subscription transition to managing another, then to secrets, then to CI pipelines. So identity in the cloud doesn’t just open apps; it opens automation, networking, and data movement. Security teams are overwhelmed by thousands of entitlements, so they stop reading them. Cloud security tools exist to manage this complexity, yet most organizations either skip them entirely or configure them so loosely they might as well not exist. Attackers reside in these unreviewed corners. The cloud console lists every misconfigured role and trust, but few people review it until the report lands.
Identity Governance Fatigue: When Visibility Isn’t Control
Many organizations are well aware of identity risks. Instead of ignoring them, they’re fatigued by it. Access reviews get scheduled, dashboards generate reports, and governance tools promise clarity, yet risky permissions remain untouched. Managers rubber-stamp approvals, orphaned accounts stay active to avoid disruption, and temporary elevated access quietly becomes permanent. So, the problem isn’t a lack of visibility; it’s a lack of enforcement. Pentesters consistently exploit this gap between policy and practice, chaining together permissions that were technically “reviewed” but never truly reduced. Visibility documents the risk. Discipline removes it. Most companies stop at documentation.
Conclusion
The pattern remains consistent: identity decisions determine everything. Controls harden, scanners improve, attack surfaces shift, and modern pentest findings still highlight overbroad rights, stale accounts, and sloppy trust relationships. So, defenders who treat identity as an HR directory problem keep losing. The smarter ones treat it as critical infrastructure. They cut privilege by default, kill legacy paths, and measure access risk with the same obsession once reserved for patch counts and CVE charts. And when that mindset finally spreads, pentest findings might briefly shift to something else again.
Respond to this article with emojis