Cloud security safeguard the applications, cloud infrastructure, and data from threats and integrates simple processes, specialized systems, and effective right practices to ascertain security without protracting the workflows that hinder
Cloud security safeguard the applications, cloud infrastructure, and data from threats and integrates simple processes, specialized systems, and effective right practices to ascertain security without protracting the workflows that hinder the software delivery. Advanced cloud security also empowers businesses to quickly identify, assess, and deal with threats across distinct cloud environments. For organizations looking to strengthen their posture, working with a specialized AWS partner like Cloudvisor ensures that infrastructure remains resilient and compliant from the very start.
Having robust cloud security is significant for making sure that data and users remain safe. However, the process of choosing the right tool for cloud security is quite tricky as you have so many factors to consider. You need to carefully analyze your priorities and figure out which tools and strategies suit you the best. In this blog, we will also explore the best 10 tools that can help you establish strong security workflows for your company. Finally, we will also see the main types of cloud security tools. You can also find valuable tips that can help you make the right decision.
Best Cloud Security Tools: A Short Summary
In this blog, we have listed the top tools that you can integrate to boost your enterprise security and ensure compliance with security standards. The list of best tools is as follows:
- Cloud Access Security Broker
- Cloud Detection and Response
- Cloud Vulnerability Management
- Cloud Infrastructure Entitlement Management
- Cloud Security Posture Management
- Cloud Workload Protection Management
- Data Security Posture Management
- Identity and Access Management
- Kubernetes Security Posture Management
- Role-based Access Control
Best 10 Cloud Security Tools
1. CASBs (Cloud Access Security Broker):
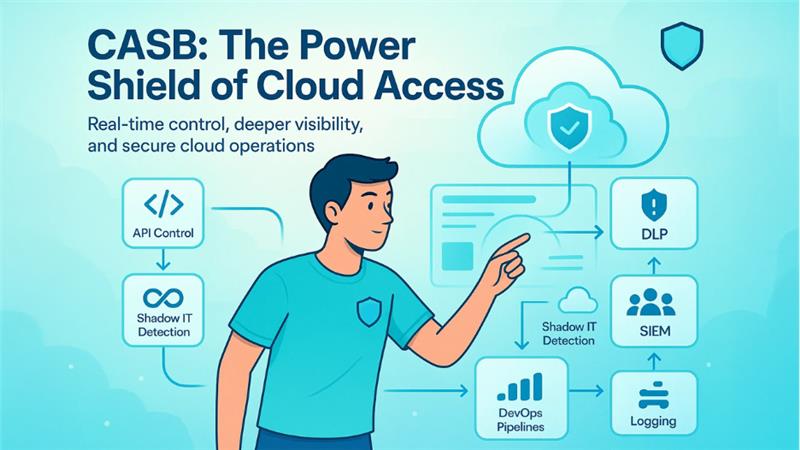
CASBs are intelligent security platforms that function as protective layer between cloud service users and providers to implement security policies, safeguard unauthorized access, and ensure in-depth insights into how teams are leveraging cloud resources. They generally work in two main ways:
API-driven Integrations: Directly connect to cloud services for post-access controls.
Proxy-driven Deployments: You can route all your traffic via an inline gateway for real-time control.
Most of the enterprise CASBs can also be directly incorporated into DevOps security workflows via REST APIs and webhooks. This enables security teams to integrate cloud access controls into CI/CD pipelines, verify policies automatically during deployment of application, and constantly track them throughout the lifecycle of the application.
CASBs effectively work with other security platforms as well. They provide shadow IT data with CIEM solution for correlation of identity, route detected data transfers to DSPM tools for categorization, ensure access logs to security data and event management platforms. Their capabilities of data loss prevention also generally integrate with present enterprise DLP platforms, which goes beyond on-premises policies into the cloud for continuous security.
2. CDR (Cloud Detection and Response):
CDR platforms introduce sophisticated threat detection capabilities to cloud environments. By integrating machine learning, behavioral analytics, and signature-driven detection, such platforms ensure consistent vigilance on your cloud setup. However, contrary to endpoint detection platforms, CDR platforms identify threats specific to cloud such as unusual API calls, suspicious resource provisioning, and privilege escalations.
Since CDR solutions leverage read-only API connections and do not need agents, they do not disturb the DevOps' workflows. A lot of these solutions also combine with CI/CD solutions so that security teams can trigger scans automatically whenever infrastructure code modifies, or new cloud resources get deployed. They generally provide support to personalizable detection rules in JSON or YML as well. These rules can easily be stored by teams with IaC (Infrastructure as code) templates in version control.
Utilizing the CDR platform analytics can help you vastly improve the wider security ecosystem by exporting priority alerts to SIEM systems with MITRE ATT&CK framework context, routing threats to SOUR platforms for planned incident responses and sharing indicators of compromise with CWPP solution for robust runtime protection. Sophisticated setups can even verify identity data with CIEM tools to highlight exposed credentials in the attack chain and request credential rotations automatically.
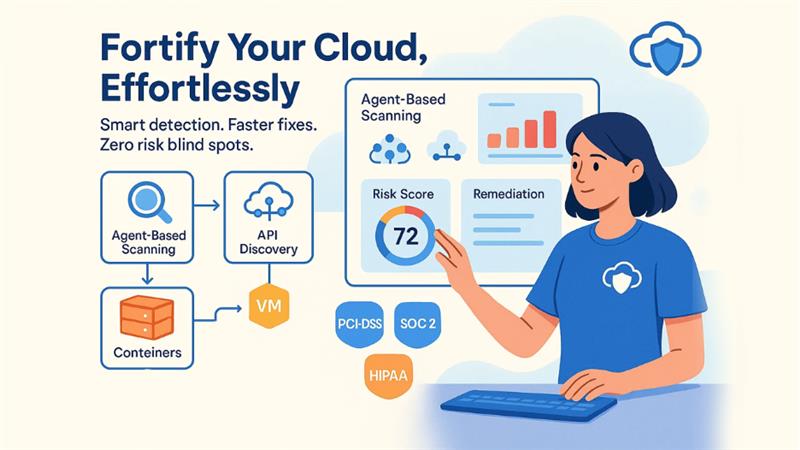
3. Cloud Vulnerability Management:

Cloud vulnerability management pertains to searching, assessing, prioritizing, and resolving security problems across platforms, cloud infrastructure, and apps. Sophisticated tools leverage techniques such as agent-driven scanning, API discovery, and network analysis to identify vulnerabilities in containers, virtual machines, managed services, and serverless machines. Numerous solutions also depend on frameworks such as Exploit Prediction Scoring System and Common Vulnerability Scoring System and then include it in the context of your environment to assess risks to your architecture.
Cloud vulnerability scanners can also combine with CI/CD pipelines via plugins so that you can check IaC templates and container images before deployment. For container environments, such tools can assess both application layers and base images as well as identify vulnerabilities in OS components and dependencies while ensuring practical remediation suggestions.
As far as compliance is concerned, such solutions effectively work with PCI-DSS, SOC 2, or HIPAA. More sophisticated platforms provide support to zero trust strategies by providing vulnerability insights in real-time for dynamic access decisions, streamlining scans across multi-cloud setups, and generating workflows to handle risks from vulnerabilities that teams cannot resolve because of business requirements.
4. CIEM (Cloud Infrastructure Entitlement Management):
CIEM platforms manage identity governance especially for cloud environments by finding, assessing, and resolving problems associated with identity consistently. Such platforms also make it quite simple to visualize and comprehend complex permission structures across multi-cloud setups by identifying excessive privileges, privilege escalation risks, and unused access rights that conventional IAM tools generally overlook.
With respect to execution, CIEM solutions can associate with cloud services and recognize providers through read-only APIs. The majority of enterprise-grade CIEM platforms directly incorporate IaC platforms such as CloudFormation, Terraform, and Pulumi. This implies that they can assess possible permission risks such as CI/CD processes and spot problems before deployment while ensuring developers get instant feedback on the IAM right practices.
CIEM findings also enhance the effectiveness of other security tools. They share identity risk information with SIEM/SOAR platforms to include context to prioritization, deliver credential exposure details to CDR tools for more effective detection of threats, and combine with CSPM solutions to connect misconfigurations with identity vulnerabilities.
Numerous CIEM platforms provide just-in-time access as well by providing temporary credentials that expire automatically after the set time or task, which minimizes standing privilege risks.
5. CSPM (Cloud Security Posture Management):
CSPM platforms ensure an effective way to ascertain governance and security in cloud environments. They manage all aspects ranging from consistent configuration checks and automated compliance tracking to risk remediation. And, if you can successfully connect CSPM platforms to cloud providers via APIs, you can establish a centralized control system across multi-cloud setups and examine thousands of configurations against compliance standards and security best practices.
Via these platforms, you can leverage policy as code frameworks such as Rego, Open Policy Agent, and Hashi Crop Sentinel. This implies that security teams determine infrastructure needs as programmable, version-controlled, and deploy it through read-only connections, which makes the setup quite simple and quick. Numerous CSPM platforms also combine with CI/CD pipelines so that developers can verify IaC templates against security policies before deployment.
Though, they comply with frameworks such as NIST 800-53, CIS benchmarks, SOC2, ISO 27001, PCI-DSS, GDPR, and HIPAA. More sophisticated characteristics of some of these platforms include drift detection. Drift detection helps spot any unauthorized changes in infrastructure and makes it quite effortless to track unauthorized processes and configuration modifications. CSPM platforms can also input misconfiguration data into vulnerability management platforms for risk scoring, ensuring resource information for CIEM tools, and combine with SOAR platforms for automated repairs.
6. CWPP (Cloud Workload Protection Management):
CWPP makes sure that your cloud workloads remain secure during runtime via platforms such as integrity checks, behavioral tracking, and threat prevention to safeguard all aspects in the compute stack, from containers and VMs to serverless functions and databases. Through tracking memory, checking processes, assessing network traffic, and verifying file integrity, CWPPs identify unusual activity before it becomes a problem. In addition, with the help of machine learning, they ensure behavioral baselines to identify anomalies such as unusual process patterns, abnormal network behavior, or suspicious API calls, all while ensuring that false positives remain minimum.
Teams generally implement these platforms as compact agents for virtual machines, API hooks for serverless functions and sidecar containers for Kubernetes to ensure that there is a balance between performance and security. Numerous CWPP platforms also combine with CI/CD pipelines by providing pre-built plugins to block vulnerable workloads and secure container images. Apart from that, runtime application self-protection includes another level of defense by recognizing and preventing attacks such as injection exploits or insecure deserialization at runtime, all without the requirement to update your application.
CWPPs provide sophisticated features such as kernel-level tracking and monitoring serverless functions, so you can incorporate runtime threat data with platforms such as CSPMs, SIEMs, and vulnerability solutions. In addition, CWPP adheres to compliance standards such as PCI-DSS, SOC-2, and GDPR with access controls, runtime audits, and workload immutability. Moreover, they allow zero trust security, secure multi-cloud setups, and complement DevOps teams with automated threat detection.
7. DSPM (Data Security Posture Management):
DSPM platforms play a crucial role in ensuring that confidential data remains safe by providing automated platforms for classification, discovery, and consistent tracking. They leverage techniques such as contextual analysis, pattern matching, machine learning, and metadata inspection to recognize sensitive data, irrespective of where you are storing it.
Such platforms depend on API-powered connectors to secure databases, cloud storage, and SaaS apps, which reduces the need for agents. They also combine with DevOps workflows to spot insecure data storage or other vulnerabilities before deployment. With characteristics such as data flow tracking, DSPM recognizes possible exposure risks and compliance issues. Numerous platforms also provide automation-powered fixes such as access control updates, encryption, and policy updates via cloud provider APIs.
As far as compliance is concerned, DSPM platforms cross-checks discovered data with regulations such as CCPA, GDPR, HIPAA, and PCI-DSS and create reports to showcase control implementation.
8. IAM (Identity and Access Management):
IAM is a robust layer for cloud environments that manages authorization, authentication, and auditing for both automated platforms and human users. Cloud-based IAM tools such as Google Cloud IAM and AWS IAM enable you to establish fine-tuned permissions via policies that determine who can do what with specific resources and in which conditions. IAM also provides support to federation protocols such as OAuth 2.0, SAML 2.0, and ODIC, which makes it quite effortless to handle identities across multiple providers and minimize administrative work.
Such platforms also interoperate with CI/CD pipelines through IaC tools, which enables development teams to determine and test access controls while automating security measures. Sophisticated setups also involve privileged access management to issue task-specific and temporary credentials with automated expiration, so elevated access is both temporary and secure.
Overall, IAM improves cloud security by offering identity context, spotting anomalies, and handling permissions with tools such as SIEM, CASBs, and CIEM. It complements zero trust policies with consistent authentication and aids with compliance (like HIPAA and SOC2) via detailed audit logs.
9. KSPM (Kubernetes Security Posture Management):
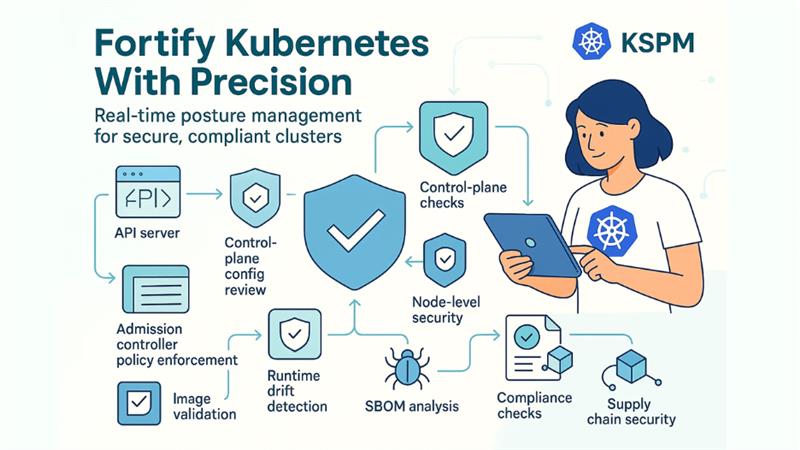
KSPM platforms specialize in making container orchestration environments secure by consistently assessing configuration continuously, checking setups, and implementing Kubernetes policies. Such platforms ensure a complete security overview across API server scans, control plane checks, workload configurations, and node-level protections.
Such solutions make the security quite simple by implementing policies during deployment with real-time admission controllers and directly interoperating in the Kubernetes environments. Teams can implement them as operators or through API connections for cluster assessments. They also operate with CI/CD tools to allow shift-level security. Main features include container image validation, runtime drift detection, analysis of software bills of materials, and supply chain security. All of this creates a robust security foundation.
KSPM can enhance security by interoperating with CWPP and CSPM to implement runtime policies, service meshes, and network policies. They ascertain compliance to main security standards such as NIST 800-53, CIS Kubernetes, and PCI-DSS as well via consistent control checks and evidence collection for containerized workloads.
10. RBAC (Role-based Access Control):
RBAC provides a straightforward way to handle permissions in cloud environments by segmenting them into roles as per the organizational functions instead of giving permissions to individual users. This simplifies complex permission sets into roles such as “application developer” or “security auditor” which admins assign as per the job responsibilities. This minimizes administrative workloads and streamlines management, especially in bigger organizations. RBAC also generally involves hierarchical structures where admins include particular privileges as required and inherit base permissions.
RBAC improves security by giving data to assess privileges, monitor compliance, and spot anomalies. Sophisticated setups even enable consistent permission management across multi-cloud environments. Such frameworks are also robust enough to help teams align with compliance standards such as ISO 27001, SOC2, and NIST 800-53 by allowing role-driven segregation of duties, audit trails, and access reviews. They provide zero-trust architecture by enabling contextual role activation as per factors such as location, device security, and resource sensitivity.
What Are the Different Types of Cloud Security Tools?
Though the blog only focuses on the best 10 cloud security solutions, several exist in the market. Mainly, they can be classified into following categories:
Cloud Security Posture Management:
CSPM (Cloud Security Posture Management) platforms automate the recognition and remediation of risks across cloud infrastructures. They render consistent compliance tracking as well as compliance checks, enabling organizations to ensure secure cloud posture. CSPM platforms inspect cloud environments for any compliance violations or misconfigurations, providing insights into security weaknesses.
Such tools aid in implementing security policies and ascertaining right practices in cloud deployments. By providing a unified view of the cloud security posture, CSPM allows proactive management of risks.
Cloud Workload Protection Platform:
CWPP solutions emphasize securing workloads across distinct cloud environments. They safeguard both hosts as well as containerized applications against evolving threats. This makes sure that overall security of cloud-driven applications and services is maintained throughout. CWPP platforms provide runtime protection, network segmentation features, and vulnerability management. The high adaptability makes them fit for multi-cloud as well as hybrid architectures.
Cloud Access Security Broker:
CASBs work as an intermediary between cloud service providers and users, implementing organizational security policies. They provide high visibility into cloud application utilization, control data access, and security risks. CASB solutions offer a wide variety of security measures, including access control, encryption, and threat prevention.
Such platforms are valuable for handling cloud access in a secure way, specifically in environments where BYOD is executed. CASBs aid in maintaining cloud usage as per the security policies, reducing the risk of unauthorized access and data leakage.
Cloud Detection and Response:
CDR platforms help in threat detection and response within cloud environments. They utilize sophisticated analytics and threat intelligence to recognize unusual activities, ensuring automated responses and real-time alerts. CDR solutions excel in resolving threats quickly, mitigating the impact on cloud resources.
By consistently assessing cloud activities, CDR platforms play a vital role in the incident response process, making sure that security teams can access vulnerabilities and attacks quite quickly.
Cloud Infrastructure Entitlement Management:
CIEM solutions handle permissions and access controls in cloud environments, avoiding the risk of excessive access rights and privileges. They allow the organizations to implement the “least privilege” principle, minimizing the risk of data breaches and unauthorized access. CIEM platforms provide insights into user activities and permission configurations, allowing more effective control over cloud resources.
Data Security Posture Management:
DSPM platforms are utilized for tracking and data security across different cloud platforms. They emphasize recognizing and reducing risks associated with data access, transfer, and storage in cloud environments. By continuously assessing data security postures, DSPM solutions allow organizations to identify misconfigurations, implement data protection policies, and ascertain compliance with data governance standards.
Such platforms also ensure visibility into areas where confidential data is stored, how it can be accessed, and by whom. This makes it simpler to handle compliance. DSPM platforms also provide support to automation-driven remediation processes, which can quickly resolve discovered vulnerabilities, minimizing the risk of data exposure.
API Security:
API security comprises technology and practices utilized to safeguard APIs from being used by malicious actors. As APIs enable the connection between distinct software services and applications, securing them is vital to avoid data breaches and ascertain integrity of software interactions.
API security platforms generally provide features such as authorization, authentication, traffic management, and threat detection. They track API traffic to detect as well as block different nefarious activities like data exfiltration or unauthorized access. Such platforms also ascertain that APIs adhere to organizational security policies.
Tips to Select the Right Cloud Security Tool
When you are choosing cloud security tools, top aspects you must keep in your mind are as follows:
Compatibility and Integration: Select tools that smoothly combine with your present cloud infrastructure and security platforms. This reduces disruptions and utilizes your present investment. It is also significant that the platform aligns with your cloud service providers and smoothly fits in your IT ecosystem, ensuring compatibility with other security solutions such as vulnerability management systems or SIEMs.
Scalability: The selected security platforms must support scalability and should improve your cloud environment. While you are dynamically scaling your cloud resources, the security tools must adjust to evolving demands without sacrificing security or performance.
Security Characteristics: Choose platforms that encompass all aspects of your cloud environment, for instance CNAPP platforms. This involves data protection, workload protection, compliance, threat detection, and network security. A tool that covers numerous security functions can minimize complexity and enhance incident response times.
AI Capabilities and Automation: To improve efficiency, search for platforms that integrate AI and automation. Such technologies can aid in fast detection of threats as well as response, minimizing the workload on security teams, and reducing human errors.
Regulatory Compliance: Make sure that security platforms align with regulatory needs with respect to your industry. This can involve robust standards for data security, privacy laws, and regulations specific to the industry. Tools that aid in ensuring compliance can help your organization avoid legal challenges and hefty fines.
Vendor Support and Reputation: Assess the vendor's reputation and the kind of support services they provide. Dependable vendor support is critical for timely troubleshooting, updates, and guidance. Furthermore, also take into account the community and ecosystem centered around additional integrations and resources.
Conclusion
Choosing the relevant cloud security platforms needs close assessment of the particular requirements of your organization, complexity of infrastructure, and compliance needs. The blog discusses the top 10 cloud security tools you can explore including CDR, CASB, Cloud Vulnerability Management, CIEM, CSPM, etc. Each tool solves a unique security challenge within cloud ecosystems. While choosing the tool, you must prioritize scalability, integration capabilities, complete security characteristics, and vendor credibility and support. Organizations can establish a powerful defense strategy. Executing a perfect combination of such platforms makes sure that there is consistent security in a constantly evolving threat landscape while ensuring regulatory compliance and operational efficiency across multi-cloud deployments.
Related Posts:
IP Security Architecture: Ensuring Secure Communication in Networks
Cloudflare Zero Trust: A Smarter Zero Trust Security Model
Respond to this article with emojis